Capturing and injecting Json values into Requests
Capturing and injecting Json values into Requests
Similar to the Authorization capture and injection you can also more generically capture JSON keys and values, and inject them into subsequent requests. You can capture a JSON token in one request and inject it into another request.
JSON Key capture is user specific so if you run in a load test each user session has its own set of captured variables which allows you to have different values for each active user session.
JSON key Capture and Injection
The process of capturing and injection is two simple steps:
- Use
WebSurge-Request-CaptureJsonTokento capture a request JSON token - Use
WebSurge-Request-InjectJsonTokento inject the captured token into target requests
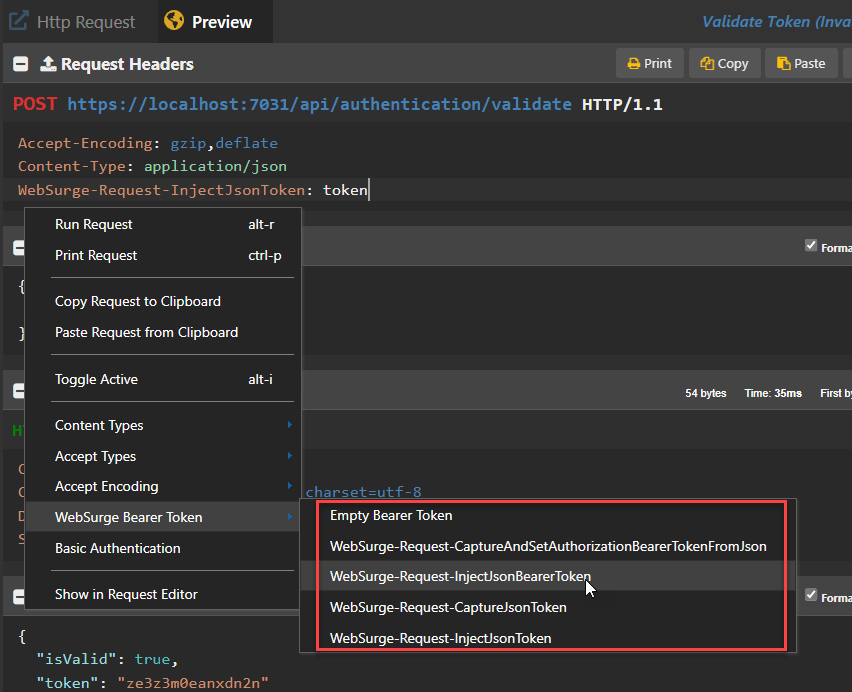
To make it easier to add these custom headers into your request's headers, you can find them on the context menu of the Request Editor:
Capture a JSON Token
To create a token use this header on the Authentication request that produces a token. The following assumes it's looking at a JSON property called token:
WebSurge-Request-CaptureJsonToken: token
Inject a JSON Token
To use the token you apply it on a request that requires the bearer token for authentication. Typically these will be update requests but may be any and all requests in an application.
To apply it to a request you'd use:
WebSurge-Request-InjectJsonToken: token
This injects the captured token named token and replaces any JSON string values named token with the captured value.
Alternately you can also specify both a token lookup key and replacement key by separating the two values with |, which allows capturing tokens from one property name, but replacing a different JSON property with the value using lookupKey|replacementKey combination:
WebSurge-Request-InjectJsonToken: token|userToken
This injects the value of the captured token value, into JSON properties named userToken. Note that the lookupKey is used the same way as a single token from the captured value with WebSurge-Request-CaptureJsonToken. The difference is that the second key replaces a property with a different name than the original token.
Example
Here's an example that demonstrates. The first request is a authentication request that returns a JSON response with a token key embedded. We use WebSurge-Request-CaptureJsonToken to capture this token key and value:
POST https://localhost:7031/api/authentication HTTP/2.0
Accept-Encoding: gzip,deflate
Content-Type: application/json
WebSurge-Request-CaptureJsonToken: token
{
username: "rstrahl@west-wind.com",
password: "kqm3ube0jnm!QKC9wcx"
}
HTTP/1.1 200 OK
Content-Length: 148
Content-Type: application/json; charset=utf-8
Date: Tue, 05 Sep 2023 21:36:32 GMT
Server: Kestrel
{
"token": "ze3z3m0eanxdn2n", /* <-- captured token */
"expiration": "2023-10-05T00:00:00Z",
"user": {
"fullname": "Rick Strahl",
"initials": "RS"
}
}
When it's time to use the token say to validate the token and see if it's valid I might send it like this using WebSurge-Request-InjectJsonToken:
POST https://localhost:7031/api/authentication/validate HTTP/2.0
Accept-Encoding: gzip,deflate
Content-Type: application/json
WebSurge-Request-InjectJsonToken: token
{
"token": "<token>"
}
This replaces the request content's body by replacing the token with the captured value from above. What is actually sent in the Http request then becomes this:
{
"token": "ze3z3m0eanxdn2n" <-- injected token
}
© West Wind Technologies, 2014-2023 • Updated: 10/24/23
Comment or report problem with topic